Model Solved Paper
For More practice questions here

1. ________ refers to a family of IEEE standards dealing with local area network and metropolitan area network.
(A)802
(B)800
(C)801
(D)803
(E) None of these
ANS:(A)
2. Which is the general network standard for the data link layer in the OSI Reference Model?
(A) IEEE 802.1
(B)IEEE 802.2
(C)IEEE 802.3
(D)IEEE 802.4
(E) IEEE 802.6
ANS:(B)
3. _________ uses a standard called IEEE 802.6.
(A)LAN
(B)WAN
(C)MAN
(D)Internet
(E) None of these
ANS:(C)
4. Repeater operates in which layer of OSI model?
(A) Application Layer
(B)Presentation Layer
(C)Physical Layer
(D)Transport Layer
(E) Data link layer
ANS:(C)
5. Where does Bridge operate in OSI model?
(A) Physical layer
(B)Data link layer
(C)Both 1 and 2
(D)Application layer
(E) None of these
ANS:(C)
6. Which of the following uses the greatest number of layers in the OSI model?
(A) Bridge
(B)Repeater
(C)Router
(D)Gateway
(E) None of these
ANS:(D)
7. Routers operate in which layer of the OSI model?
(A) Physical layer
(B)Data link layer
(C)Network layer
(D)All of these
(E) None of these
ANS:(D)
8. Modem is a _______ that modulates and demodulate signals.
(A) DCE (Data circuit terminating equipment)
(B)DTE(Data terminal equipment)
(C)DTE-DCE
(D)Both 1 and 2
(E) None of these
ANS:(A)
9. A communication network which is used by large organization over regional, national or global area is called_______
(A)LAN
(B)WAN
(C)MAN
(D)Internet
(E) None of these
ANS:(B)
10. At _______ layer, TCP/’IP defines two protocols: Transmission Control Protocol (TCP) and User Datagram Protocol (UDP)
(A) Transport layer
(B)Network layer
(C)Physical layer
(D)Application layer
(E) None of these
ANS:(A)
11. The _______ layer is the layer closest to transmission medium.
(A)Transport
(B)Network
(C)Data link
(D)Physical
(E) None of these
ANS:(D)
12. End to end connectivity is provided from host to host in:
(A) Network layer
(B)Session layer
(C)Data link layer
(D)Transport layer
(E) None of these
ANS:(D)
13. Which of the following TCP/IP protocol is used for transferring electronic mail messages from one machine to another?
(A) SNMP
(B)SMTP
(C)RPC
(D)FTP
(E) None of these
ANS:(B)
14. Which of the following is an example of a client server model?
(A) FTP
(B)DNS
(C)TELNET
(D)All of these
(E) None of these
ANS:(D)
15. Which IEEE standards is used for Wi/Fi system?
(A)802.11
(2B802.1
(3C802.2
(4D802.3
(5)E802.10
ANS:(A)
16. __________ is the continuous ability to send and receive data between interconnected networks
(A) FTP
(B)SMTP
(C)TNS
(D)Network Interoperability
(E) None of these
ANS:(D)
17. What is the default subnet mask for a class B network?
(A) 127.0.0.1
(B)255.0.0.0
(C)255.255.0.0
(D)255.255.255.0
(E) None of these
ANS:(C)
18. What is loopback address?
(A) 127.0.0.1
(B)255.0.0.0
(C)255.255.0.0
(D)127.0.0.0
(E) None of these
ANS:(A)
19. Internet like network within enterprises.
(A)Intranet
(2BSwitching alternating
(3)Cnter organization networks
(4)Dxtranets
(5) Eone of these
ANS:(A)
20. A central computer surrounded by one or more satellite computers is called a
(A) Bus network
(B)Ring network
(C)Star network
(D)All the above
(E) None of these
ANS:(C)
21. With an IP address of 100, you currently have 80 subnets. What subnet mask should you use to maximize the number of available hosts?
(A) 192
(B)240
(C)248
(D)224
(E) 252
ANS:(E)
22. Encryption/decryption provides a network with __________
(A)Privacy
(B)Authenticity
(C)Contiguity
(D)on-repudiation
(E) None of these
ANS:(A)
23. The data to be encrypted at the sender site is called ______. The data to be decrypted at receiver end is called _________.
(A) Secret key, public key
(B)Public key, secret key
(C)Plaintext, cipher text
(D)Cipher text, plaintext
(E) None of these
ANS:(C)
24. In digital signature the private key is used for ______ and the public key for ______.
(A) Encryption, decryption
(B)Decryption, encryption
(C)Plaintext, cipher text
(D)Cipher text, plaintext
(E) None of these
ANS:(A)
25. A __________ -‘s main purpose is to prohibit unauthorized access to your computer via the Internet.
(A) Popup blocker
(B)Firewall
(C)Spyware
(D)Spam assassin
(E) None of these
ANS:(B)
26. To create a copy files in the event of system failure, you create a ________.
(A) Firewall
(B)Redundancy
(C)Backup
(D)Restore file
(E) None of these
ANS:(C)
27. Print server uses _______ which is a buffer that holds before it is send to the printer.
(A) Queue
(B)Spool
(C)Node
(D)Stack
(E) None of these
ANS:(B)
28. Which of the following identifies specific web page and its computer on the web page?
(A) Website
(B)URL
(C)Web site address
(D)Domain Name
(E) None of these
ANS:(D)
29. __________ is the computer to computer exchange of routine business data between trading partners in standard data formats.
(A) CTS
(B)DSR
(C)VDR
(D)EDI
(E) None of these
ANS:(D)
30. Communication handler is basically an _______ 16 bit micro controller?
(A) 8085
(B)8086
(C)8086A
(D)80C186
(E) None of these
ANS:(D)
31. Which uses a pre-shared key that is more than 7 and less than 64 characters in length?
(A) WPA-PSK
(B)TKIP
(C)AES
(D)All the above
(E) None of these
ANS:(D)
32. Ping command is used for what purpose?
(A) Test a device on a network whether it is reachable
(B)Test a hard disk fault
(C)Test a bug in the application
(D)Test a device scanning quality
(E) None of these
ANS:(A)
33. Two different kind of networks can be connected by using _____
(A) Bridges
(B)Satellite
(C)Gateway
(D)Routers
(E) None of these
ANS:(C)
34. Full adder is used to ______
(A) 2 bit addition
(B)3 bit addition
(C)4 bit addition
(D)6 bit addition
(E) None of these
ANS:(B)
35. Most important advantages of an IC is its __________
(A) Easy replacement in case of circuit failure
(B)Low power consumption
(C)Extremely high reliability
(D)Reduced cost
(E) None of these
ANS:(C)
36. An IC contains 50 gates each of which consists of 6 components/ It’s belong to
(A) VLSI
(B)LSI
(C)MSI
(D)SSI
(E) None of these
ANS:(C)
37. Which type of computers use the 8 bit code called EBCDIC?
(A) Mini computers
(B)Mainframe computers
(C)Super computers
(D)Micro computer
(E) None of these
ANS:(B)
38. An AND gate
(A) Implement logic addition
(B)Is equivalent to a series switching circuit
(C)Is any-or all gate
(D)Is equivalent to a parallel switching circuit
(E) None of these
ANS:(B)
39. The decimal equivalent of the binary number 11100001111 is
(A) 1806
(B)1807
(C)2806
(D)All the above
(E) None of these
ANS:(B)
40. Programs in which of the following memories can’t be erased?
(A) RAM
(B)ROM
(C)Cache memory
(D)Virtual memory
(E) None of these
ANS:(B)
41. The IP address 135.0.10.27 belongs to address class?
(A) A
(B)B
(C)C
(D)D
(E) None of these
ANS:(B)
42. Which are not used in case of applet?
(A)Read/write
(B)Internet
(C)Search engine
(D)All the above
(E) None of these
ANS:(A)
43. Which of the following is not a type of database?
(A) Hierarchical
(B)Relational
(C)Network
(D)Transition
(E) None of these
ANS:(D)
44. Which of the following is not a type of SQL statement?
(A) Data Manipulation Language
(B)Data Definition language
(C)Data control language
(D)Data standard language
(E) None of these
ANS:(D)
45. In QUEUE, the item deleted at one end is called_____
(A) Rear
(B)Front
(C)Top
(D)Base
(E) None of these
ANS:(B)
46. The drawback of the binary tree sort are remedied by the_______
(A) Linear sort
(B)Heap sort
(C)Insertion sort
(D)Quick sort
(E) None of these
ANS:(B)
47. White Box testing a software testing technique is sometimes called_____
(A) Graph testing
(B)Basis path
(C)Glass box testing
(D)Data flow testing
(E) Loop testing
ANS:(C)
48. Which of the following is used with database?
(A) EDI
(B)Credit card
(C)ATM
(D)Payment gateway
(E) Data mining
ANS:(E)
49. When a cracker attempts to misuse or steal data from a system, it is called_______
(A) Stealing
(B)Intrusion
(C)Virus
(D)Worm
(E) None of these
ANS:(A)
50. To modify existing rows of the table __________ statement is used.
(A) ALTER
(B)MODIFY
(C)UPDATE
(D)COMMIT
(E) DELETE
ANS:(C)


 20:49
20:49
 ibpsrecruitmentguru
ibpsrecruitmentguru





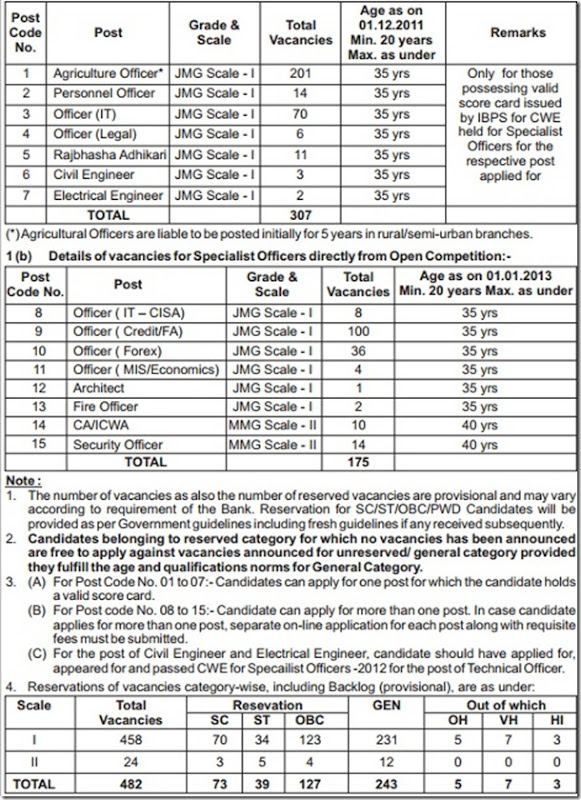
 Dena Bank announced recruitment for Specialist Officer jobs 2013.Candidates required to apply online who qualified IBPS SO CWE .
Dena Bank announced recruitment for Specialist Officer jobs 2013.Candidates required to apply online who qualified IBPS SO CWE .